A vulnerability management program identifies, evaluates, prioritizes, and mitigates vulnerabilities that could compromise an enterprise's infrastructure and applications. A modern vulnerability management program integrates automation, threat intelligence, and data science to predict which vulnerabilities pose the greatest risk to a given environment. This is a key component in setting up a successful Cybersecurity program within your organization or for your clients.
Vulnerability Management by the Numbers
In recent years, the number of vulnerabilities discovered in devices, networks, and applications has increased dramatically. According to the National Vulnerability Database, the number of Common Vulnerabilities and Exploits (CVEs) has more than tripled since 2016. (Identity Theft Resource Center® (ITRC))
Highly sophisticated efforts to exploit those vulnerabilities are also on the rise. The number of reported data breaches increased 17% between 2018 and 2019, according to the Identity Theft Resource Center (ITRC). In just the first two months of 2020, 11.476 breaches exposed 1.66 billion records.
Yet most companies are still not adequately prepared. Cybercriminals are becoming more advanced and organizations are struggling to ensure their team's cybersecurity skill sets, tools, and processes can address these threats. All this comes at a real cost to businesses. By 2025, Cybersecurity Ventures predicts damages caused by cybercrime will cost the world $6 trillion annually (up from $3 trillion in 2015)-costs that, in a time of historic economic disruption, businesses can scarcely afford.
As vulnerabilities and diversified attacks continue to grow, you need a vulnerability management program to properly protect your infrastructure, applications, and data that is also a part of your overall Cybersecurity Program.
Traditional Vs. Risk-Based Vulnerability Management
Risk-based vulnerability management is a more modern alternative to traditional methods that combines data science, real-time vulnerability intelligence, and automation to create a prioritized and efficient approach to better isolating and understanding the risks that actually pose a real threat to an organization. Companies are turning to risk-based vulnerability management to save time, create more efficient remediation workflows, and lower their risk profile.
According to leading analysts, the future of vulnerability management programs is risk-based. In recent months, as vulnerabilities and threats continue to increase and evolve, Gartner has recognized the necessity for vulnerability prioritization based on risk. "Gartner has called out the critical need to assess assets for configuration issues and vulnerabilities, and to be able to prioritize what you do with that assessment, based on the risk to your organization." [Gartner, Inc.: Market Guide for Vulnerability Assessment, Craig Lawson, Mitchell Schneider, Prateek Bhajanka, Dale Gardner, Nov. 20, 2019.]
Building A Vulnerability Management Program
Organizations looking to establish or strengthen their vulnerability management programs should begin by following these six key st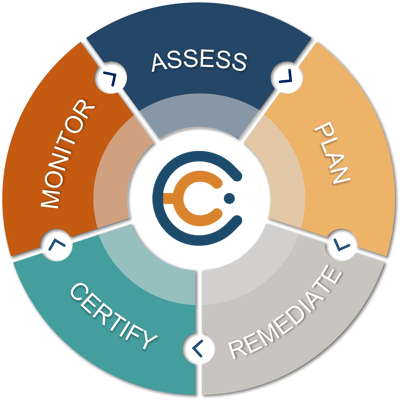 eps.
eps.
- Assemble your team: Start laying the groundwork for your program by identifying all the key players needed. You will need a manager or engineer tasked with handling vulnerability management and at least one analyst who identifies, tracks, and assesses vulnerabilities across your environment or potentially your client environments.
- Acquire the right tools: A vulnerability management solution makes sense of and sorts this acquired data, which identifies the top vulnerabilities that pose the greatest risk to the organization. These are then fed into a remediation workflow (typically using a ticketing system) which is shared with IT and DevOps.
- Cross-reference the threat landscape: Take your understanding of your assets and known vulnerabilities within the organizations you are managing and cross-reference them with your threat intelligence. This will help you determine the impact of a potential exploit-another key factor in determining risk.
- Know the assets, applications, and risk tolerance: To develop a detailed asset inventory, look to automated tools to help with this discovery task (most MSPs\MSSPs have these in place), which will scan the organization to identify assets like servers, workstations, virtual machines, storage arrays, and network devices. The risk tolerance might be informed by the industry or specific company guidelines.
- Measure, evaluate, and prioritize your vulnerabilities: When considering the right platform for your organization, look for one that integrates real-world vulnerability intelligence, data science, automated risk analysis, customized risk metrics, and even risk-based SLAs. The best modern platforms combine all this into a metric or score that is simple, understandable, and repeatable. Centrum Cyber does just that.
- Communicate, remediate, and report: Your vulnerability management solution should facilitate rather than obstruct key team communication. It should also help you remediate quickly and efficiently while keeping everyone informed and making reporting on your progress simple and intuitive. Centrum Cyber does just that as well.
Integrate a Risk-Based Vulnerability Management into Your Cybersecurity Program
The need for a modern vulnerability management program in a business is obvious. Using traditional vulnerability management methods leaves remediation teams chasing down vulnerabilities that may not reduce their overall risk and creates inefficiencies in workflows. Modern vulnerability management programs enable organizations to take a proactive, data-driven approach to threats and streamline internal operations to save time and money, reduce wasted efforts, improve team collaboration, and make a significant impact on their risk profiles.
Learn how Centrum Cyber along with its integrations with Tenable® and Sentinel One® can help you implement this modern approach and maintain your Cybersecurity Program from a single source of truth.